Upon vaults are always end-to-end encrypted, and are the only encrypted inheritance vault provider with a public whitepaper.
Only accessibly by you and your beneficiaries
Upon vaults are only ever accessible by vault owners and their beneficiaries. Even Upon cannot read your vault.
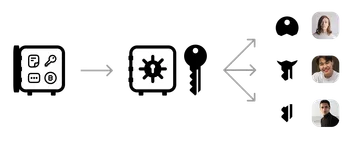
End-to-end encryption
Only you and your beneficiaries can access your vault data. The vault is encrypted with keys that only you and your beneficiaries possess, meaning no third party can ever read your data, even Upon.
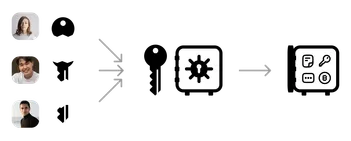
Beneficiary key sharing
Your vault key is split between your beneficiaries, meaning a minimum number of your beneficiaries are required to reconstruct the full key together to decrypt your vault.